4. Virtual LAN (VLAN) and VLAN
Trunking
Virtual
LAN
4.1 A Virtual
LAN (VLAN) is a broadcast domain
created based on the functional, security, or
other requirements, instead of the physical locations of the devices, on a switch or
across switches. With VLANs, a switch can group different interfaces into different
broadcast domains. Without VLANs, all interfaces of a switch are in the same broadcast
domain; switches connected with each other are also in the same broadcast
4.2 Different
ports of a switch can be assigned to different VLANs. A VLAN can also span multiple
switches (i.e. have members on multiple switches).
4.3 The
advantages of implementing VLAN are:
_ It
can group devices based on the requirements other than their physical
locations.
_ It
breaks broadcast domains and increases network throughput.
_ It provides better security by separating devices into different
VLANs.
_ Since
each VLAN is a separate broadcast domain, devices in different VLANs cannot listen
or respond to the broadcast traffic of each other.
_ Inter-VLAN
communication can be controlled by configuring access control lists on the router
or Layer 3 switch connecting the VLANs.
4.4 VLANs can
be configured using one of the following two methods:
Static
VLAN
_ Assigning
VLANs to switch ports based on the port numbers.
_ It
is easier to set up and manage.
Dynamic VLAN
_ Assigning
VLANs to switch ports based on the MAC addresses of
the devices connected to
the ports.
_ A
VLAN management application is used to set up a database of MAC addresses, and configure
the switches to assign VLANs to the switch ports dynamically based on the
MAC addresses of the connected devices. The application used by Cisco switches
is called VLAN Management Policy Server (VMPS).
4.5 Cisco
switches support a separate instance of spanning tree and
a separate bridge table for each VLAN.
4.6 A VLAN
is different from an IP subnet in concept.
However, there is a one-to-one relationship between a VLAN and an IP subnet. It
means that devices in the same VLAN are also in the same IP subnet, devices in different
VLANs are also in different IP subnets.
4.7 Conventional
switching (i.e. Layer 2 switching) cannot
switch frames across VLANs.
4.8 To forward
packets between VLANs, a router or
a Layer 3 switch is required.
4.9 A router
can route traffic between different VLANs by having a physical interface connected to
the switch for each VLAN. Each interface is connected to an access
link of the switch . The default
gateway of the hosts of each VLAN should be configured as the interface of the router
connected to that VLAN.
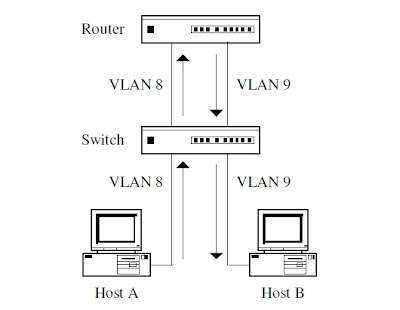
4.10 For
example, if Host A in VLAN 8 sends a packet to Host B in VLAN 9, the packet
will be forwarded
to the router's interface for VLAN 8 because it is the default gateway of Host A (and
other hosts in VLAN 8). The router will then route the packet out the interface for VLAN 9 (the VLAN of
Host B) based on IP routing . The switch will then forward the packet to Host
B.
4.11 If a
router supports VLAN trunking, it can route traffic between different VLANs by having only
one physical interface connected to the switch. The interface should be connected to a
trunk link of the switch carrying traffic
for all the VLANs . This type of configuration is sometimes
called "router on a stick".
4.12 A Layer
3 switch is a switch with routing features. It uses
specialized hardware (Application
Specific Integrated Circuits, ASICs) to route packets between VLANs or IP subnets.
Therefore, it is more efficient than routers. Moreover, VLAN routing does not involve
processing of the Layer 3 header of the packets.
VLAN
Trunking
4.13 There are
two different types of links in a switched network:
Access
link - a link that is part of only one VLAN.
Therefore, a port connected to an access link
can be a member of only one VLAN.
Trunk
link - a 100 Mbps or 1000 Mbps point-to-point link
that connects switches or routers, and
carries frames of different VLANs. Therefore, a port connected to a trunk link can
be a member of multiple VLANs. All VLANs are configured on a trunk link by
default.
4.14 VLAN
Trunking, by making use of frame tagging, allows
traffic from different VLANs to transmit through the same Ethernet link (trunk
link) across switches.
4.15 VLAN Trunking identifies the
VLAN from which a frame is sent by tagging the frame
with the
source VLAN ID (12-bit
long). This feature is known as frame
tagging or frame identification.
4.16 With
frame tagging, a switch knows which ports it should forward a broadcast frame (forward out
the ports which have the same VLAN ID as the source VLAN ID). It also knows which
bridge table it should use for forwarding an unicast frame (since a separate bridge table
is used for each VLAN).
4.17 A frame
tag is added when a frame is forwarded out to a trunk link, and is removed when the frame is
forwarded out to an access link. Therefore, any device attached to an access link is
unaware of its VLAN membership.
4.18 Cisco
switches support two trunking protocols:
Inter-switch
Link (ISL)
_ It
is a Cisco proprietary VLAN trunking
protocol and can only be used between Cisco switches
or switches supporting ISL.
_ It
encapsulates a frame by an ISL header and trailer.
_ An
ISL header is 26 bytes long and contains the
12-bit VLAN ID, MAC addresses of
the sending and the receiving switch, and some other information.
_ An
ISL trailer is 4 bytes long and contains the
CRC of the frame.
_ It
supports a separate instance of spanning tree for each VLAN by using a Cisco proprietary
feature called Per-VLAN Spanning Tree (PVST+).
Different instances of
spanning tree allow the STP parameters of different VLANs to be configured
independently. For example, we can break a network loop by blocking
different links for different VLANs instead of blocking the same link for all VLANs, so
that the available bandwidth can be used more efficiently.
IEEE 802.1q
_ It
is the IEEE standard trunking protocol.
_ It
inserts a 4-byte header to
the middle of the original Ethernet header. The 802.1q header contains the 12-bit
VLAN ID and some other information.
_Recalculation of the FCS is required after the insertion of the 802.1q header as the original header has been changed.
Ethernet frame without 802.1q
header
Dest.
addr.
(6 bytes)
|
Dest.
addr.
(6 bytes)
|
Type
(2 bytes)
|
Data
(46-1500 bytes)
|
FCS
(4 bytes)
|
With 802.1q header
Dest.
addr.
(6 bytes)
|
Source
addr.
(6 bytes)
|
802.1q
header
(4 bytes)
|
Type
(2 bytes)
|
Data
(46-1500 bytes)
|
FCS
(4 bytes)
|
_Recalculation of the FCS is required after the insertion of the 802.1q header as the original header has been changed.
_ It
did not support a separate instance of spanning tree for each VLAN originally. However, Cisco
switches can use PVST+ with 802.1q to
support this feature. IEEE has also
defined a new specification called 802.1S,
which can be used with802.1q to support multiple instances of spanning tree.
_ It
defines one VLAN as the native VLAN.
It does not insert 802.1q header into the frames
sent from the native VLAN over a trunk link. The default native LAN is VLAN
1.
_ Since
802.1q is defined as a type of Ethernet frame, it does not require that every device on a
link understands 802.1q. By defining a trunk port as a member of the native
VLAN, any Ethernet device (even if it does not understand 802.1q) connected to
the trunk port can read frames for the native VLAN.
_ Both
sides of a trunk link must agree on which VLAN is used as the native VLAN. Otherwise, the trunk will
not operate properly.
VLAN
Trunking Protocol (VTP)
4.19 VLAN
Trunking Protocol (VTP) is a Cisco proprietary protocol for
switches to exchange VLAN
configuration information (e.g. VLAN membership). It ensures the configuration
information is consistent across a VTP domain.
For example, you only need to create
a VLAN (or define the name of a VLAN, etc.) on one switch, and VTP will
distribute that information to all switches in the VTP domain automatically.
There is no need to
repeat the configuration works manually on each switch. All devices that need to share
VLAN information must use the same VTP domain name.
4.20 Switches
exchange VLAN configuration information using VTP
advertisements.
Some of the
information included in a VTP advertisement are:
_ Configuration
revision number.
_ Configuration
information for each VLAN, e.g. the VLAN ID, VLAN name, and switches which
have ports that are members of the VLAN.
4.21 A device
running VTP operates in one of the following three modes:
Server
mode
_ A
VTP server can create, update, and delete VLANs and VTP information in a VTP domain.
_ A
VTP server increments the configuration revision number when there is a change to the
VLAN configuration information.
_ A
VTP server floods VTP advertisements to the VTP servers and clients in the VTP domain
every 5 minutes or when there is a change to the VLAN configuration
information.
_ When
a VTP advertisement with a higher revision number is received, the stored VLAN
configuration information is updated.
_ A
VTP server saves the VLAN configuration information in NVRAM (Nonvolatile RAM).
Client
mode
_ A
VTP client cannot create, update, or delete the VLAN configuration information in
a VTP domain.
_ A
VTP client receives and forwards VTP advertisements from the other VTP switches in
the same VTP domain, and learns the VLAN configuration information
from the advertisements.
_ A
VTP client does not save the VLAN configuration information in NVRAM.
Transparent
mode
_ A
switch in transparent mode does not participate in any VTP domain. It can create,
update, and delete the VLAN configuration information with only local significance,
i.e. the changes only affect that switch and will not be sent to other switches.
_ A
switch in transparent mode receives and forwards VTP advertisements from other VTP
switches but ignore the information in the advertisements.
_ A
switch in transparent mode saves the locally defined VLAN configuration information in
NVRAM.
4.22 There
must be at least one VTP server in a VTP domain.
4.23 To
configure a switch as a VTP server, first configure it as a VTP client such
that it can receive the
updated VLAN configuration information from the other VTP switches. After that, it
can be configured as a VTP server.
4.24 VTP
Pruning prevents broadcast frames and unicast frames
for a particular VLAN from being
forwarded to the switches that do not have any port with membership of that VLAN. It allows more efficient
use of network bandwidth.
No comments:
Post a Comment